Email is crucial for business communication but faces increasing cyber threats. To combat phishing and fraud, Microsoft will require strict email authentication (SPF, DKIM, and DMARC) for Outlook and Hotmail users sending over 5,000 daily emails, starting May 5, 2025. Here's how to comply.
What’s Changing?
Microsoft's New Requirements (Starting May 2025):
- Affects senders sending over 5,000 daily emails
- Must implement SPF, DKIM, and DMARC protocols
- Non-compliance risks emails going to spam or being blocked
Industry-Wide Movement:
- Follows similar changes by Google and Yahoo in 2024
- Part of a broader effort to combat email threats
- Creates stronger email security standards
Why This Matters for Your Business
If your business uses email to reach customers, this is a big deal. Ignoring the new email rules could cause all the emails you are sending to Microsoft users to end up in the junk folder, or not get delivered at all. Over time, this can make email providers see you as untrustworthy and affect your reputation.
On the flip side, following these rules does more than just keep you out of the spam box. It makes your business look more trustworthy, and it makes your emails more likely to land in inboxes. Plus, it stops scammers from pretending to be you, which builds trust with your audience and protects your reputation.
What are DMARC, SPF, DKIM & BIMI ?
Email authentication helps protect against spam and fraud by verifying that emails really come from who they claim to be. Here's how it works:
- SPF: This is your guest list. It lists the tools allowed to send emails for your domain. When an email arrives, Outlook checks this list to confirm the sender's legitimacy.
- DKIM: This is your seal of authenticity. It attaches a digital signature to your emails, letting recipients verify that the message hasn't been altered in transit, and it's also proof your email is genuine.
- DMARC: The rule maker. It decides what to do with emails that don't pass earlier checks like SPF or DKIM.
- Let them go through the inbox
- Flag them as suspicious and quarantine them (spam folder)
- Block them completely so they never reach the inbox.
- BIMI: Think of this as your email's verified profile picture. Just like a blue checkmark on social media, it shows your official logo next to your emails in the inbox, making it easy for people to know it's really from your company.
These protocols work together to keep your emails safe. They check that your emails really come from you and haven’t been changed, and they let you decide what to do with the ones that are flagged.
Your Compliance Checklist
Ready to get started? Here’s a simple roadmap to ensure your emails meet Microsoft’s new rules:
1. Audit Your Setup
Check your current email authentication status by using Palisade’s Microsoft Compliance Checker to review your SPF, DKIM, and DMARC configurations to get a baseline understanding of your existing setup.
2. Start DMARC setup
Set up DMARC with a policy of p=none to start monitoring your email traffic without disrupting delivery. This will provide insights into how your emails are being authenticated.
Your DMARC record set to none typically looks like this:
3. Analyze Reports and Wait for a Full Cycle
Wait for a full cycle, meaning the time it takes for all your email-sending applications to send data and analyze the DMARC reports you receive. A full cycle usually last a few days to a few weeks depending on your email volume.
4. Set Up SPF and DKIM Properly
With the data from your DMARC reports, you can now configure SPF and DKIM accurately, ensuring only legitimate emails pass authentication.
- Update your DNS with an SPF record listing only authorized mail servers. Make sure to avoid exceeding the 10 DNS lookup limit, which could cause authentication issues.
- Generate and publish a DKIM key, which will act as your digital signature for your email services, proving their authenticity.
5. Gradually Shift DMARC Policy
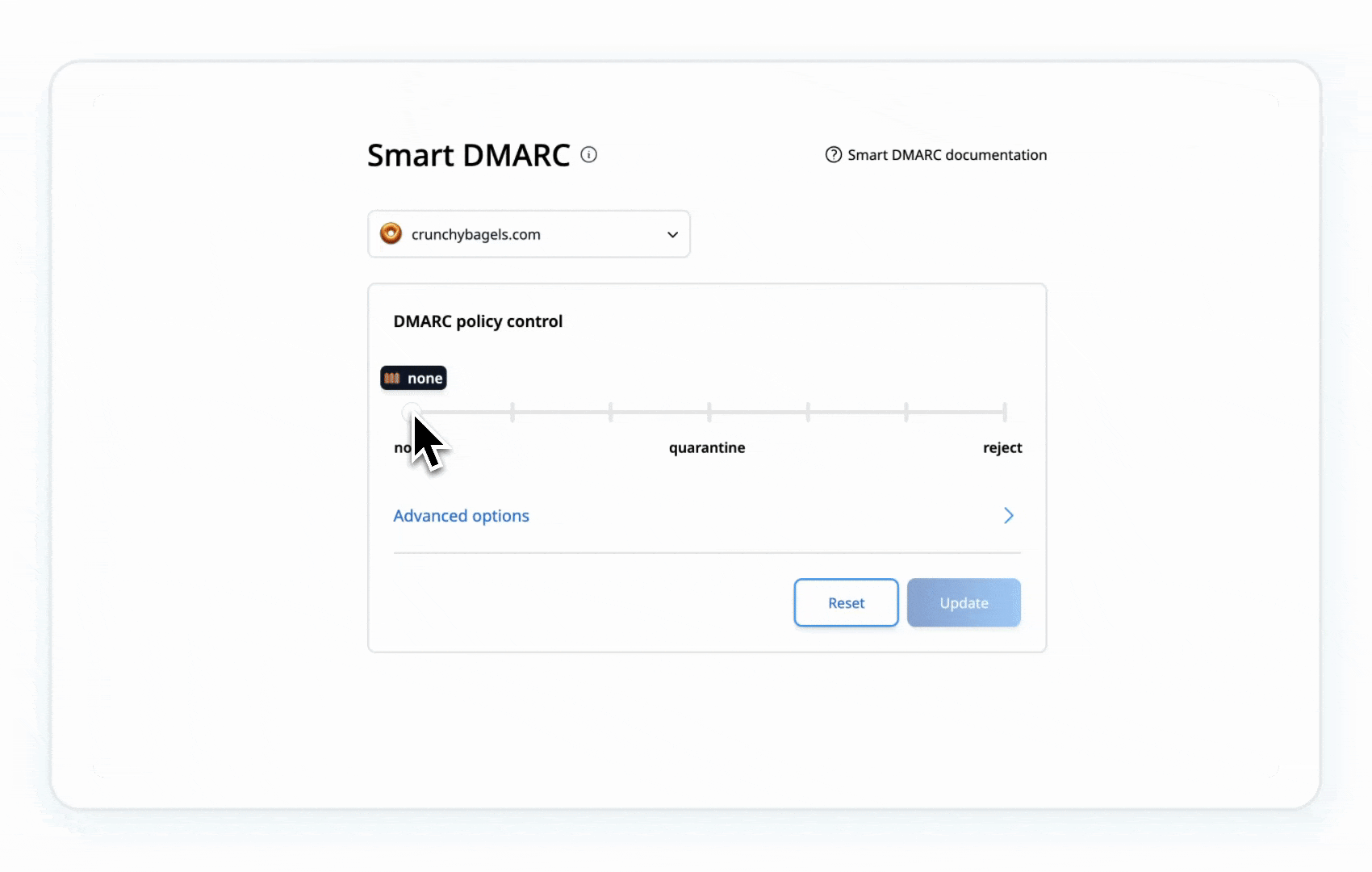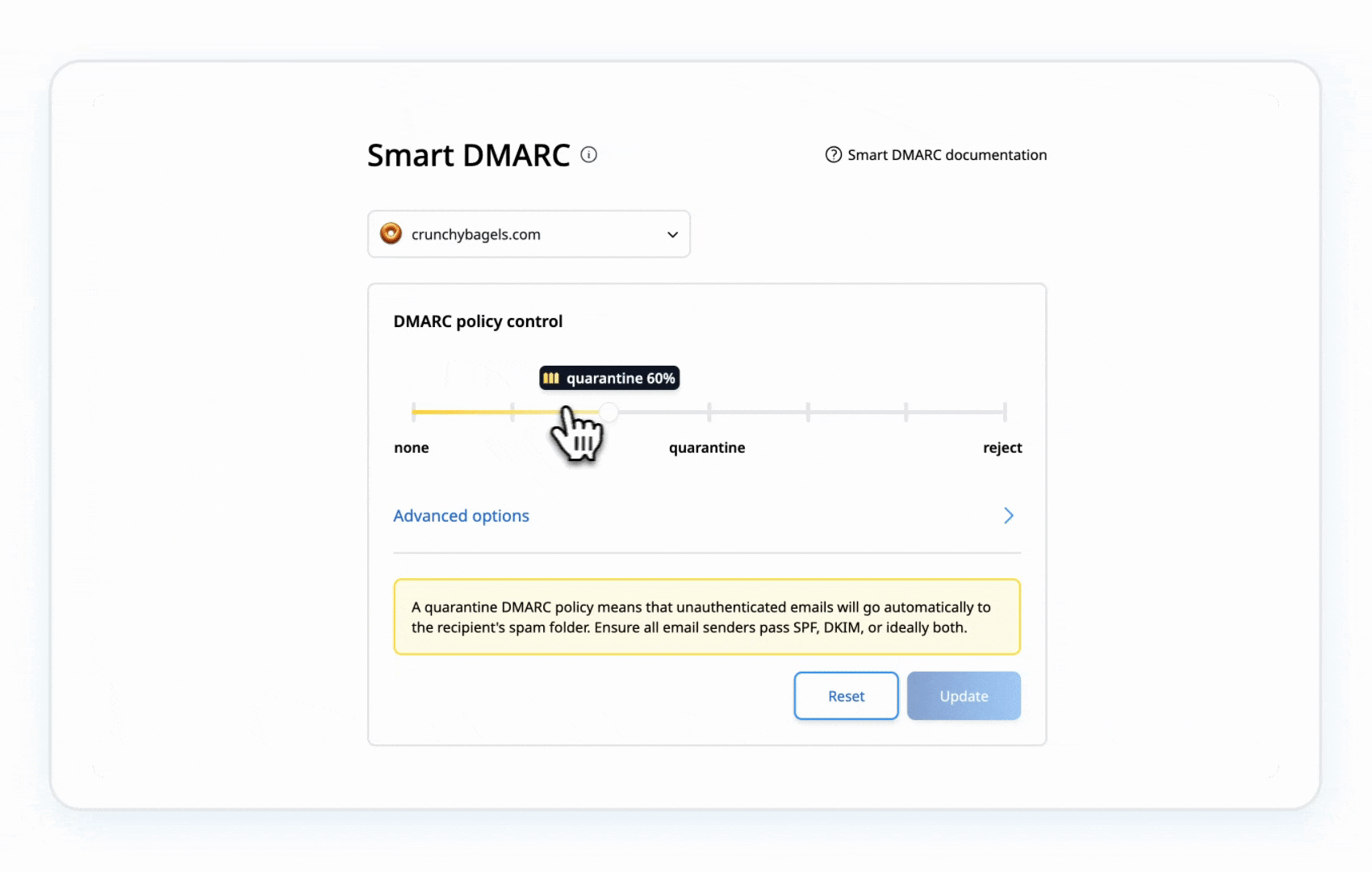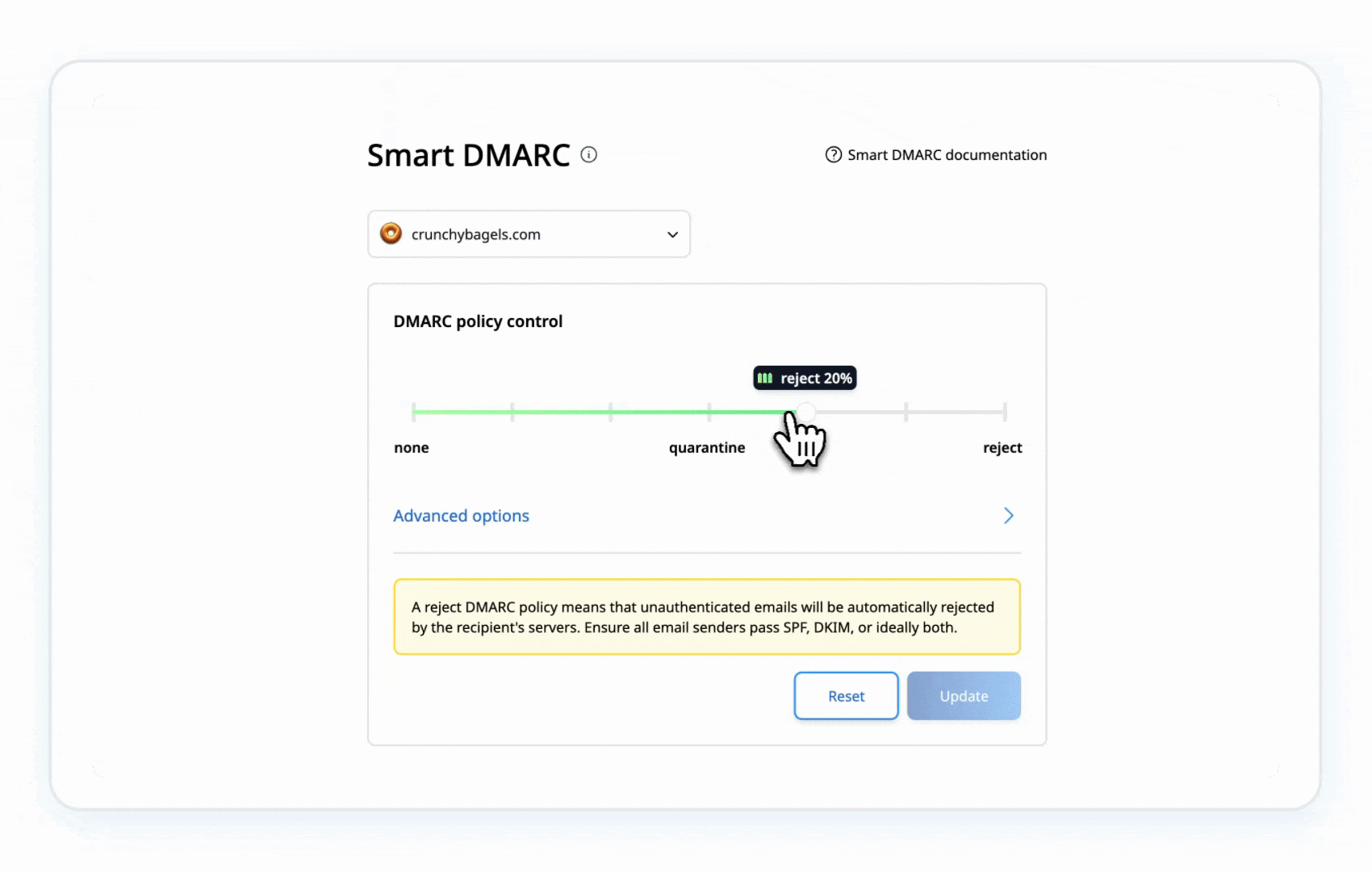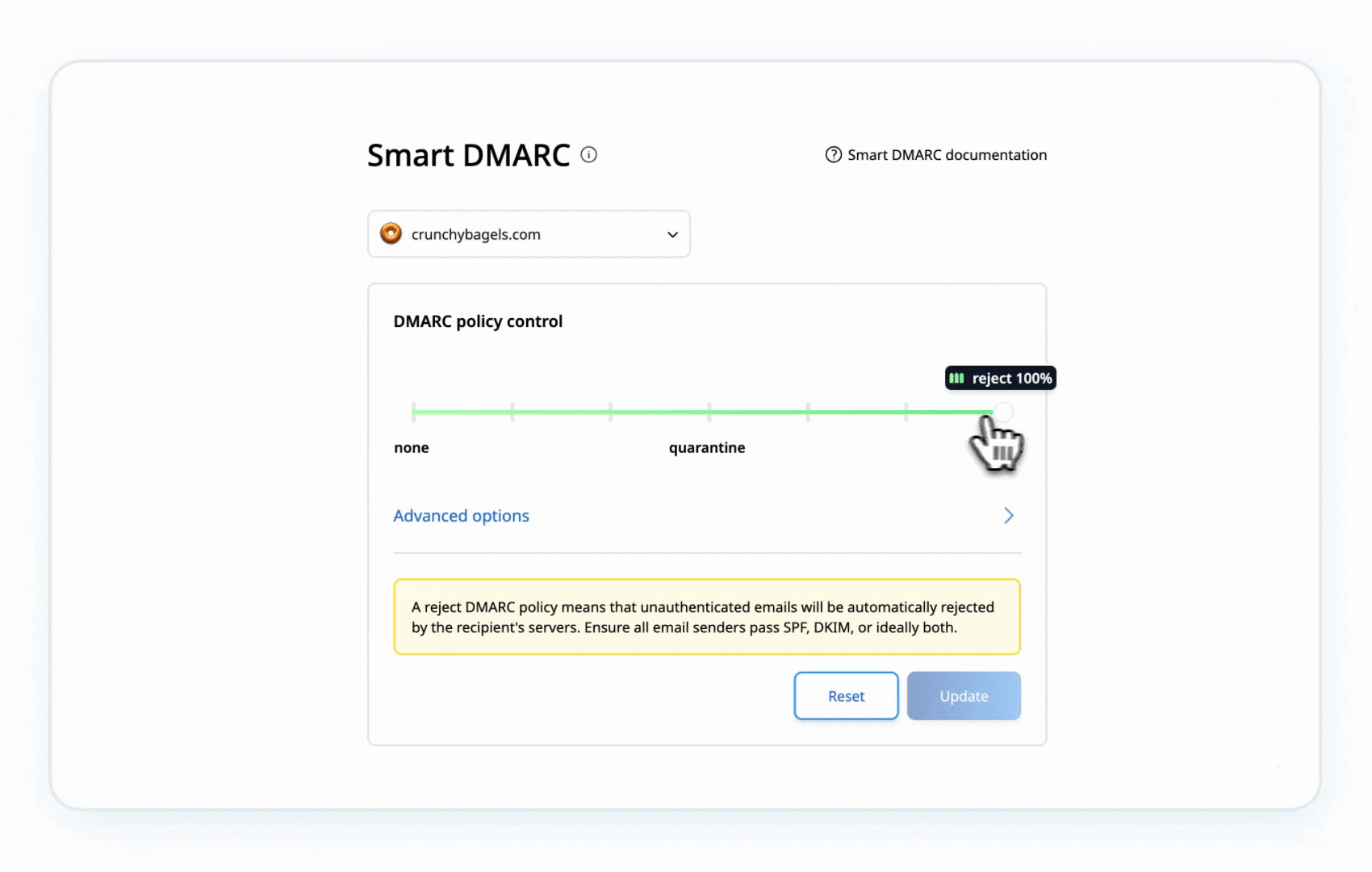
Once SPF and DKIM are correctly set up, move your DMARC policy from p=none to p=quarantine (to send suspicious emails to spam), and eventually to p=reject (to block unauthorized emails entirely). Gradually tightening your DMARC policy allows you to monitor and adjust without disrupting legitimate email delivery.
Example of a DMARC policy set to Quarantine:
Example of a DMARC policy set to Reject:
Even if these steps are pretty straightforward, they can still feel technical. That’s where our WorkBench solution, your partner in compliance comes into play by simplifying the whole process with the click of a button, ensuring your business meets Microsoft’s standards without any headaches.
- Easy Setup: We configure SPF, DKIM, and DMARC for you, tailored to your needs.
- Real-Time Monitoring: Our platform tracks your email performance, delivering clear reports to keep you informed.
- Deliverability Boost: We optimize your settings to maximize inbox placement and security.
Recommended Email Hygiene Tips
Large-scale senders should follow these key practices, to maintain trustworthiness and good deliverability.
- Valid P2 (Primary) Sender Addresses: Make sure the “From” or “Reply-To” address is legitimate, aligns with the actual sending domain, and is capable of receiving responses.
- Effective Unsubscribe Options: Include a simple, prominent method for recipients to opt out of future emails, especially for marketing or high-volume campaigns.
- Email List Maintenance & Bounce Handling: Routinely clean out invalid addresses to minimize spam reports, bounced emails, and unnecessary sends.
- Honest Email Practices: Craft truthful subject lines, steer clear of misleading headers, and confirm that recipients have agreed to receive your communications.
Adhering to these best practices is always highly recommended, regardless of whether you send a high volume of emails or not. Outlook may impose penalties, such as filtering or blocking senders who fail to comply, particularly in cases of significant authentication or hygiene violations.
Don’t wait for May 2025 to roll around. Start preparing today to keep your emails flowing smoothly. Sign up for our WorkBench solution to ensure compliance with Microsoft’s new requirements. In a world where every email counts, compliance isn’t just mandatory, it’s your competitive edge.
Frequently Asked Questions (FAQ)
- What are Microsoft’s new email rules starting May 2025?
- Senders of over 5,000 daily emails to Outlook and Hotmail users must implement SPF, DKIM, and DMARC protocols. Non-compliance may lead to emails being marked as spam or blocked.
- Why is Microsoft enforcing these changes?
- To combat phishing and fraud, these rules enhance email security by verifying sender authenticity, aligning with industry efforts from Google and Yahoo.
- Who do these requirements apply to?
- They target senders exceeding 5,000 daily emails to Microsoft users, but all senders benefit from adopting these standards.
- What happens if I don’t comply?
- Non-compliant emails risk landing in spam folders or being blocked, potentially harming your sender reputation and deliverability.
- What are SPF, DKIM, DMARC, and BIMI?
- SPF: Lists authorized servers for sending emails from your domain.
- DKIM: Adds a digital signature to verify email authenticity.
- DMARC: Sets rules for handling emails failing SPF/DKIM checks (allow, quarantine, or block).
- BIMI: Displays your logo in inboxes, signaling verified emails.
- How can I comply with Microsoft’s requirements?
- Audit your SPF, DKIM, and DMARC setup.
- Start with a DMARC policy of p=none to monitor traffic.
- Analyze DMARC reports over a cycle (days to weeks).
- Configure SPF and DKIM accurately.
- Gradually shift DMARC to p=quarantine, then p=reject.
- What tools can help with compliance?
- Solutions like Palisade’s Smart Dmarc simplify setup, monitor performance, and optimize SPF, DKIM, and DMARC for better deliverability.
- What are DMARC reports, and why are they important?
- DMARC reports show how your emails authenticate, helping you identify unauthorized senders and refine your setup.
- Why should I clean my email lists?
- Regularly removing invalid or inactive addresses reduces bounces, spam complaints, and costs while improving deliverability.
- What’s an effective unsubscribe option?
- A clear, easy-to-use link in your emails that allows recipients to opt out of future messages, especially for marketing campaigns.
- Do I need to comply if I send fewer than 5,000 emails daily?
- While not mandatory, adopting these practices protects your reputation and aligns with industry standards.
- Can I use a third-party email vendor and still comply?
- Yes, but you must ensure SPF, DKIM, and DMARC are configured for your domain, coordinating with your vendor.
- What are honest email practices?
- Use truthful subject lines, avoid misleading headers, and ensure recipients have opted in to receive your emails.
- When should I start preparing?
- Start now to avoid disruptions by May 2025. Early compliance ensures smooth delivery and a stronger sender reputation.
.png)






.png)

.png)