.png)
If you’re running into the 550 5.7.515 Access denied error, we totally get it, it’s frustrating, and you’re not alone. Your emails to Outlook and Hotmail users are getting blocked, and it’s happening because Microsoft is cracking down on email security with new, stricter rules since May 5, 2025. No more sliding into the Junk folder; if your emails don’t comply, they’re stopped cold. You just want your messages to get through, and we’re here to make that happen.
The short version? Microsoft is tightening things up to fight phishing and fraud, and that means your emails need to check all the right boxes, like SPF, DKIM, and DMARC. But don’t stress, we’ll help you fix this error fast and keep your emails flowing. Let’s sort it out, step by step.
Microsoft’s Outlook new email authentication requirements
Microsoft’s latest security update is a bold move to fight against phishing and fraud, with a focus on companies sending over 5,000 daily emails per day. Here’s what’s happening:
- Strict Enforcement since May 5, 2025: All senders must implement SPF, DKIM, and DMARC authentication protocols. Non-compliant emails will be rejected immediately, not sent to the Junk folder as initially planned.
- Immediate Rejection Policy: Microsoft scrapped the Junk folder routing for better user security and to reduce confusion. If your emails fail authentication, they’ll trigger the error: "550 5.7.515 Access denied, sending domain [YourSendingDomain] does not meet the required authentication level."
- Industry Alignment: This follows Google and Yahoo’s 2024 push for stricter email standards, signalling a broader shift toward a safer email ecosystem.
For high-volume senders, compliance is critical, there’s no grace period.
Consequences of non-compliance
Ignoring Microsoft’s requirements could damage your email operations. Here’s what’s at stake:
- Blocked Emails: As mentioned earlier, since May 5, 2025, non-compliant emails will be rejected right away, stopping your messages from reaching recipients.
- Damaged Sender Reputation: Repeated rejections can flag your domain as untrustworthy, hurting deliverability across other email providers like Gmail or Yahoo.
- Lost Business Opportunities: Blocked emails mean missed customer engagements, poor marketing campaign results, and potential revenue losses.
- Customer Lost Trust: If scammers spoof your domain due to weak authentication, your brand’s credibility could take a hit.
Compliance isn’t just about avoiding errors, it’s about protecting your business’s communication lifeline and your brand reputation.
What is the 550 5.7.515 access denied error?
The 550 5.7.515 Access denied error is an SMTP response from Microsoft indicating that your email failed authentication checks. This error will be triggered by:
- Missing Authentication Records: No SPF, DKIM, or DMARC records set up for your domain.
- Misconfigured Records: Errors in SPF, DKIM, or DMARC configurations, such as incorrect syntax or outdated entries.
- Domain Misalignment: The “From” header domain doesn’t match the domains in your SPF or DKIM signatures.
- No DMARC Policy: A missing or disabled DMARC policy (e.g., not set to p=quarantine or p=reject).
This error means your emails are blocked, and recipients won’t see them. It’s a hard stop that demands immediate action.
How to fix the 550 5.7.515 access denied error
The 550 5.7.515 Access Denied error can be really discouraging, your emails aren’t getting through, and it’s tough to know why. This error pops up when Microsoft’s security rules flag something off with your email setup, specifically your SPF, DKIM, or DMARC settings. Don’t worry if those sound technical, we’ll break them down together and guide you through fixing them.
Step 1: Audit your setup
Let’s start by figuring out where things stand. Use Palisade’s Email Score tool to check your current SPF, DKIM, and DMARC records. It’s like a friendly detective that scans your setup and tells you what’s missing or not quite right, maybe an outdated SPF record or a DKIM key that’s not set up yet. This takes just a few minutes and gives you a clear picture to work from.
Step 2: Set up DMARC monitoring:
Next, let’s set up a basic DMARC policy to watch what’s happening with your emails.
Automated set up: use Palisade to set up your DMARC policy automatically.
Manual set up: Start with a DMARC policy of p=none to monitor email traffic without blocking:
Here’s what this does:
- p=none means no emails get blocked, it’s just watching.
- rua=mailto:reports@example.com tells servers to send you reports about your email traffic.
- use your own email address here.
Think of it like installing a security camera, you’re not locking anything down yet, just keeping an eye on things. If you’re unsure how to add this to your DNS, your domain provider’s support team can help, or Palisade’s tools can guide you.
Step 3: Analyze DMARC reports
Now, let those reports roll in. Depending on how many emails you send, wait a few days, or up to a couple of weeks if your volume is lower. These reports are like a logbook: they’ll show if your emails are passing authentication (great!) or if something’s failing (like an unauthorized sender sneaking in). Look for patterns, maybe a third-party service you use isn’t listed in SPF, or DKIM isn’t signing emails properly. It’s not the most exciting read, but it’s your key to spotting the problem.
Step 4: Configure SPF and DKIM properly
With your reports in hand, let’s tackle the two big players: SPF and DKIM.
- SPF: This is your “approved sender list.” Update your DNS to include only the mail servers you trust, like your email provider (e.g., Google Workspace) or marketing tool (e.g., Mailchimp). Be careful: SPF has a limit of 10 DNS lookups.
- DKIM: This adds a digital signature to your emails, proving they’re really from you. You’ll need to generate a DKIM key and publish it in your DNS. It’s like a tamper-proof seal on a letter.
These fixes close the gaps that Microsoft’s checks.
Step 5: Strengthen your DMARC policy gradually
Once SPF and DKIM are properly configured, you can tighten security with DMARC:
- Step 5a: Move to p=quarantine:
This flags suspicious emails (e.g., putting them in spam) without rejecting them outright. Test it for a week or so, check your reports to make sure legit emails aren’t getting caught.
- Step 5b: When you’re confident, go to p=reject:
Now, unauthorized emails get blocked completely. It’s the ultimate shield against this error.
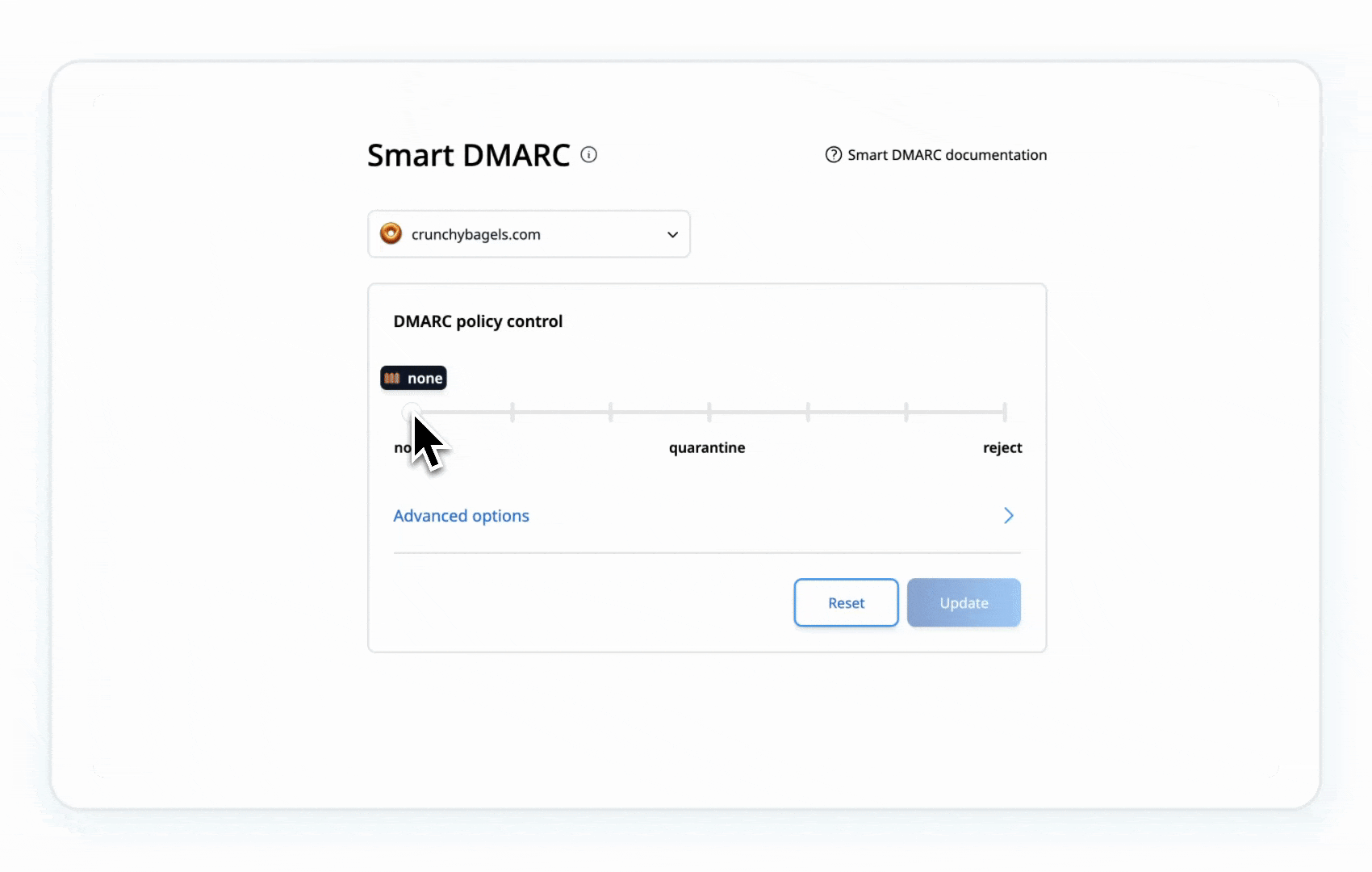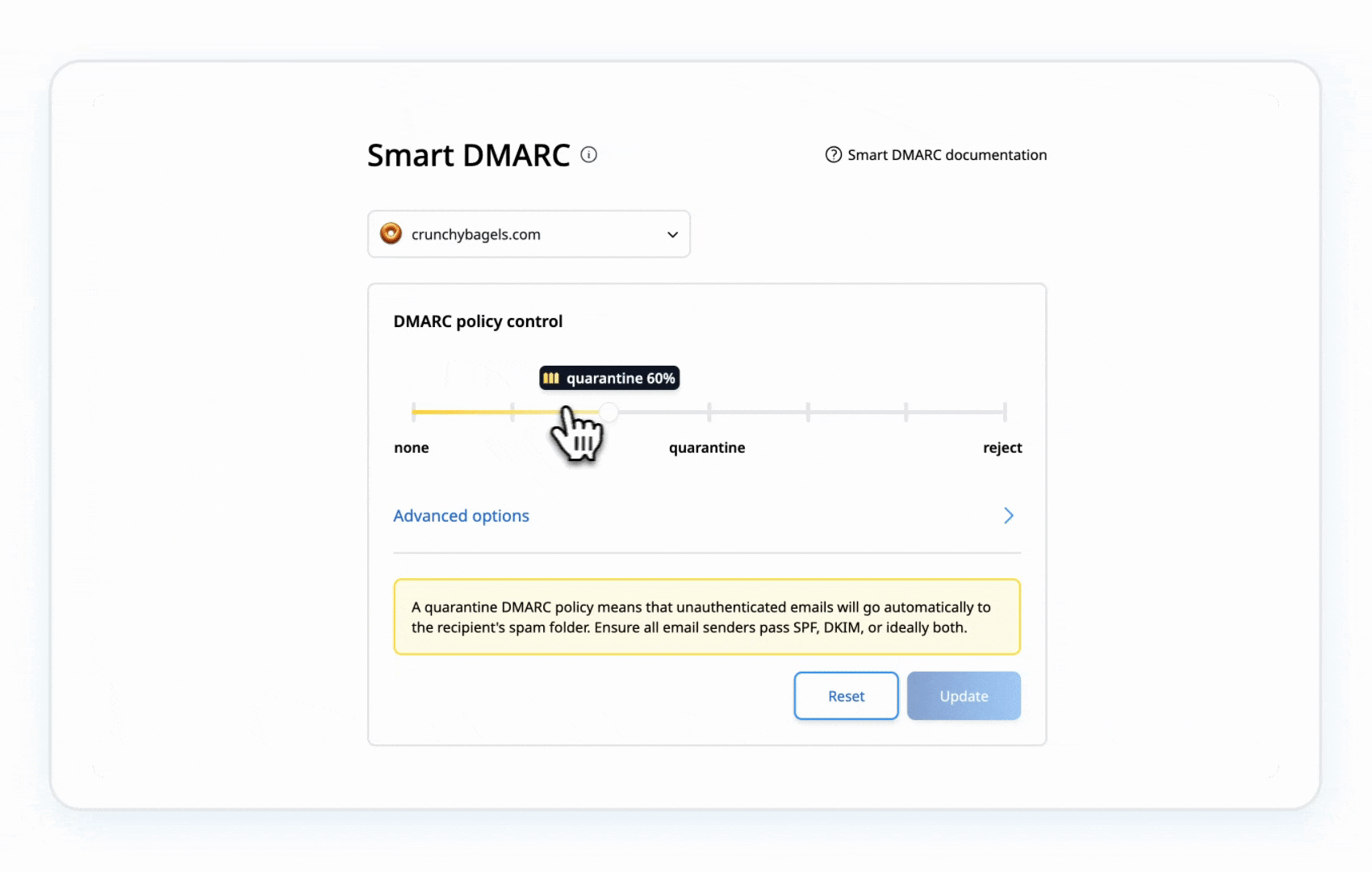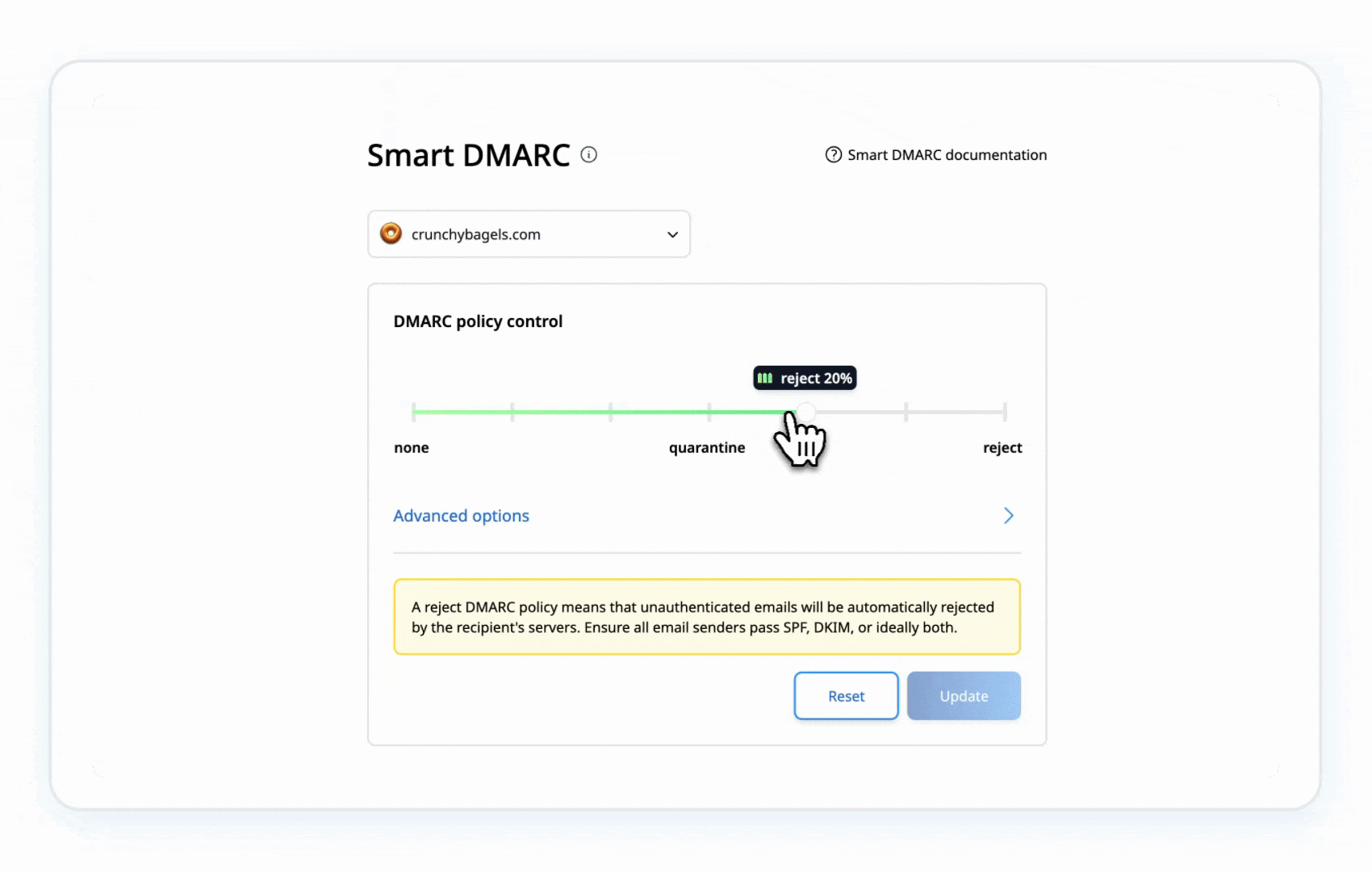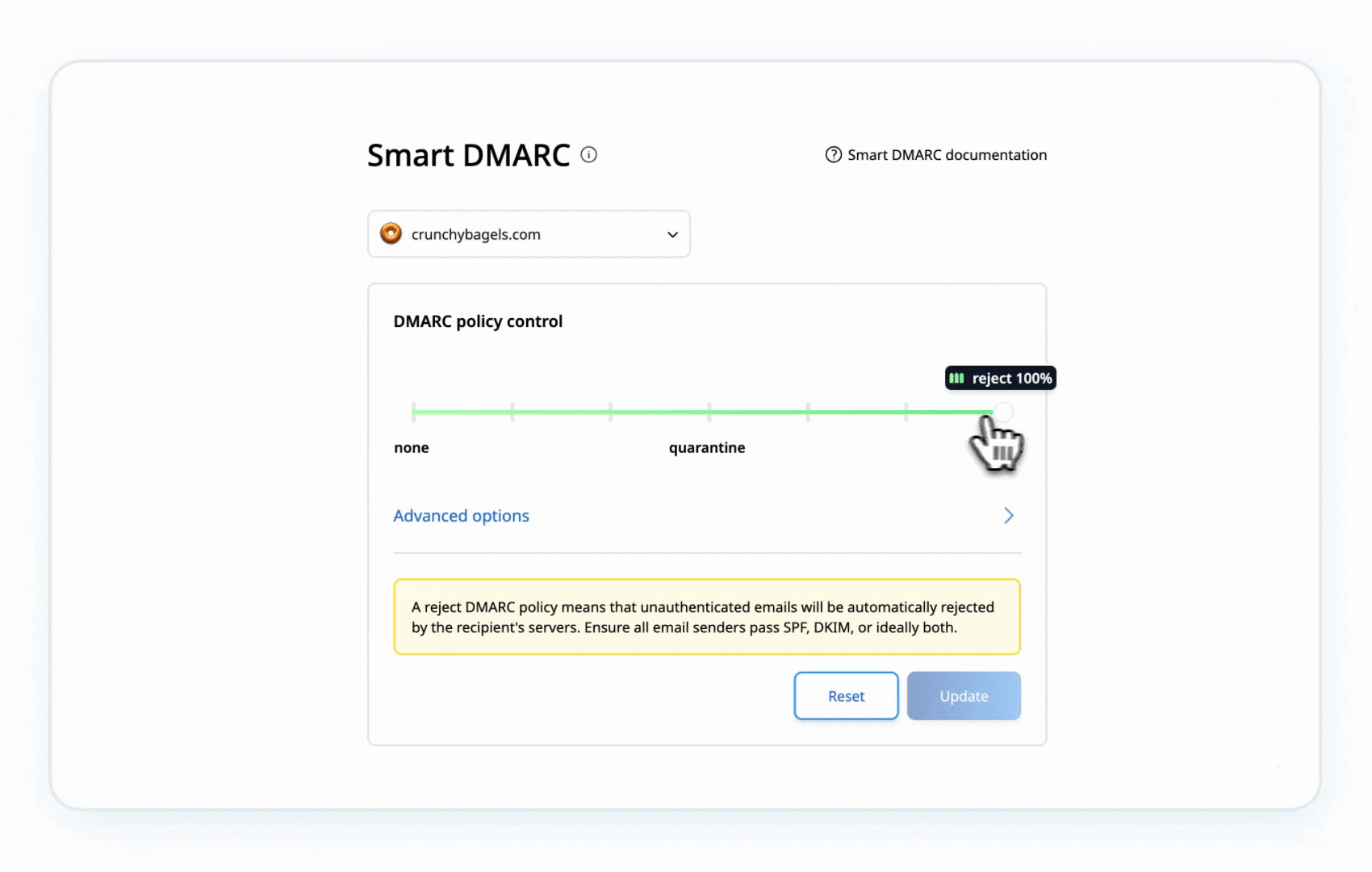
This gradual shift keeps things safe without disrupting your email flow. You’re in control here.
Summary: What you’ve done and what’s next
Let’s recap all the actions you’ve just taken to tackle that 550 5.7.515 error, step by step, without any extra fluff. Here’s what you did:
- Checked your setup with the Email Score tool to find the weak spots.
- Started monitoring with DMARC to see what’s really happening.
- Analyzed reports to pinpoint issues like unauthorized senders.
- Fixed SPF and DKIM to lock down who can send emails as you.
- Implemented DMARC reject policy to prevent 550 5.7.515 error.
What’s next? Your emails should start passing Microsoft’s checks, and that 550 5.7.515 error will fade away. Keep an eye on those DMARC reports for a bit to ensure everything’s running smoothly. If anything pops up, or if this still feels overwhelming, Palisade’s DMARC agebt can handle all of this for you. We’re here to make this as easy as possible, so you can get back to what you do best, knowing your emails are secure and delivered.
Quickly resolve the 550 5.7.515 error with Palisade’s AI
Palisade’s AI-Assisted Workflow is your go-to solution for resolving the 550 5.7.515 Access denied error while protecting your email system from a wide range of issues. We don’t just stop at fixing this specific error, our tool tackles other common email errors like SPF misalignments, DKIM signature failures, or DMARC misconfigurations, and defends against security threats like phishing and spoofing. With 24/7 monitoring, we ensure your domain stays secure and compliant at all times, so you won’t have to deal with errors like these ever again.
Palisade’s AI-Assisted Workflow makes it effortless:
- Quick Setup: Automates SPF, DKIM, and DMARC configuration in minutes.
- User-Friendly for All: If you’re not a technical person, our AI will do the tech work for you, making setup simple and stress-free.
- Stress-Free Monitoring: Delivers clear reports and real-time alerts to keep you informed.
- Proven Results: Maximizes deliverability to keep your emails in inboxes.
Frequently asked questions (FAQ)
- What is the 550 5.7.515 Access denied error? It’s an SMTP error from Microsoft indicating your email failed SPF, DKIM, or DMARC authentication, resulting in rejection.
- Why is Microsoft enforcing these new rules? To counter phishing and fraud, and ensure only authenticated emails reach Outlook and Hotmail users, aligning with industry standards.
- What happens if I don’t comply? Your emails will be rejected, disrupting communication, damaging your sender reputation, and potentially costing revenue to your business.
- Who needs to comply with these requirements? All senders, especially those sending over 5,000 daily emails to Outlook or Hotmail users, must implement SPF, DKIM, and DMARC.
- How can Palisade help me avoid the 550 5.7.515 error? Palisade’s AI-Assisted Workflow automates SPF, DKIM, and DMARC setup, and ensures compliance with 24/7 monitoring to keep your emails secure and your email deliverability strong.
- What triggers the 550 5.7.515 error? Missing or misconfigured SPF, DKIM, or DMARC records, domain misalignment, or a disabled DMARC policy can cause this error.
- Do I need to comply if I use a third-party email vendor? Yes, even if you are using a third-party tool, you must ensure your domain’s SPF, DKIM, and DMARC records are correctly configured.
- When should I start preparing? Now! The new Microsoft requirements are already in effect.
- Does Microsoft’s new DMARC requirement affect me if I’m not a bulk sender? Absolutely, even if you’re sending fewer than 5,000 emails daily to Outlook and Hotmail users, compliance is essential to avoid the 550 5.7.515 Access denied error.
.png)






.png)

.png)