.png)
If you heard of DMARC to protect your domain and though that was interesting (and a bit complicated), we have news for you: It’s about to get a facelift. To help you guys distill that, here’s the TLDR resumed in the simplest terms.
The TLDR: DMARCbis for dummies:
DMARCbis is the upcoming upgrade to DMARC, the protocol that helps verify if emails actually come from the domains they claim to. Originally launched in 2015, DMARC has become a key defense against email spoofing and phishing. But it has limits—like being hard to understand, struggling with complex email setups, and not always working well with forwarded emails. DMARCbis, developed by the Internet Engineering Task Force (IETF), fixes many of these issues.
It adds clearer rules, better tools for managing tricky domain structures (like government subdomains), and smarter reporting to help organizations monitor their email security more effectively. It introduces new features like the DNS Tree Walk algorithm (a better way to find domain policies), simplifies confusing tags, and gives domain owners more control. DMARCbis is still in draft, but it’s expected to become an official standard in 2025.
Why Do We Need DMARCbis?
While the current original DMARC (RFC 7489) is great, it isn’t perfect. It has unclear sections, struggles with complex domain setups (like Public Suffix Domains), and doesn’t fully address issues like email forwarding breaking authentication. DMARCbis tackles these pain points by:
- Making the protocol easier to understand and implement.
- Adding flexibility for diverse email environments.
- Improving reporting to help organizations monitor their email security.
Think of DMARCbis as a polished, more user-friendly DMARC that keeps the core mission, stopping phishing and spoofing, while adapting to modern email challenges.
Key Features of DMARCbis
DMARCbis isn’t a complete rewrite; it builds on the original DMARC with specific improvements.
Here’s what’s new:
- Clearer Guidelines
- The spec is reorganized for readability, with better examples and precise terms (e.g., DMARC policy is now Domain Owner Assessment Policy).
- It’s split into three RFCs: the main protocol, aggregate reporting, and failure reporting, making it easier to navigate.
- Full Participation Rules
- A new section defines what it means to “fully participate” in DMARC. Domain owners must send SPF- and DKIM-aligned emails, publish DMARC records, and analyze reports. Email receivers must verify records, perform alignment checks, and send daily reports.
- Updated DMARC Tags
- New tags like np (for non-existent subdomains), psd (for Public Suffix Domains), and t (for testing mode) give domain owners more control.
- Old tags like pct (percentage sampling), rf (report format), and ri (report interval) are retired to simplify things. Don’t worry, DMARC records still use v=DMARC1.
- Smarter Domain Discovery
- DMARCbis replaces the Public Suffix List with a DNS Tree Walk algorithm to identify Organizational Domains. This makes it easier for complex setups, like gov.uk, to use DMARC effectively.
- Better Reporting
- Aggregate reports are stricter, with an updated XML format that includes new tags and reflects real-world practices. This helps organizations get clearer insights into their email performance.
What is the DNS Tree Walk algorithm?
The DNS Tree Walk algorithm, introduced in DMARCbis, offers a smarter way to understand complex Organizational Domains for DMARC policy records and email alignment. Unlike the older Public Suffix List method, which struggled with complex setups, this algorithm starts at a subdomain and climbs up the domain hierarchy, checking for a DMARC record at each level, up to eight steps, until it finds one. This makes it both precise and adaptable, especially for tricky domain structures.
Let’s take for example, gov.uk, a Public Suffix Domain (PSD) used by the UK government. With the old method, a subdomain like london.gov.uk was seen as a separate Organizational Domain, complicating consistent DMARC policies across subdomains.
The DNS Tree Walk algorithm simplifies this:
- Step-by-step: For schools.london.gov.uk, it checks _dmarc.schools.london.gov.uk, then _dmarc.london.gov.uk, and up to _dmarc.gov.uk, stopping when it finds a policy.
- Flexible control: The psd tag lets owners define how their domain works. If gov.uk sets psd=n, it unifies all subdomains under one Organizational Domain. If psd=y at london.gov.uk, that subdomain can stand alone with its own policy.
DNS Tree Walk example for schools.london.gov.uk:
This new method is perfect for a cleaner, more flexible way to manage DMARC policies and boost email security.
How to Prepare for DMARCbis
Preparing for DMARCbis starts with a solid foundation. While this article focus is on DMARC & DMARCbis it’s important to note that DMARC doesn’t operate alone, SPF and DKIM work hand in hand with DMARC to ensure your emails are authenticated properly. Without proper SPF and DKIM configuration, your DMARC setup won’t be effective.
1. Audit Your Setup
Begin by checking your current email authentication status. Use Palisade’s free Email Score tool to review your SPF, DKIM, and DMARC configurations. This gives you a baseline understanding of your existing setup and highlights any areas that need attention.
.png)
2. Start DMARC Setup
If you haven’t set up DMARC yet, start by creating a basic policy with p=none. This setting allows you to monitor your email traffic without blocking or redirecting anything, giving you valuable insights into how your emails are being authenticated.
Here’s an example DMARC record:
3. Analyze you DMARC Reports
After setting up DMARC, wait for a full email cycle, typically a few days to a few weeks, depending on your email volume. This ensures all your email-sending applications have sent data. Review the DMARC reports you receive to understand your email flows, identify legitimate sources, and spot potential unauthorized senders.
4. Set Up SPF and DKIM Properly
Using the insights from your DMARC reports, configure SPF and DKIM accurately. These two protocols are critical because DMARC relies on them to verify your emails:
- SPF: Update your DNS with an SPF record that lists only your authorized mail servers. Keep it tight, exceeding the 10 DNS lookup limit can cause authentication failures.
Example SPF record:
- DKIM: Generate a DKIM key and publish it in your DNS. This acts as a digital signature, proving your emails’ authenticity. Coordinate with your email service provider to ensure it’s implemented correctly.
Without proper SPF and DKIM setups, DMARC’s alignment checks will fail, leaving your domain vulnerable. Take the time to get these right.
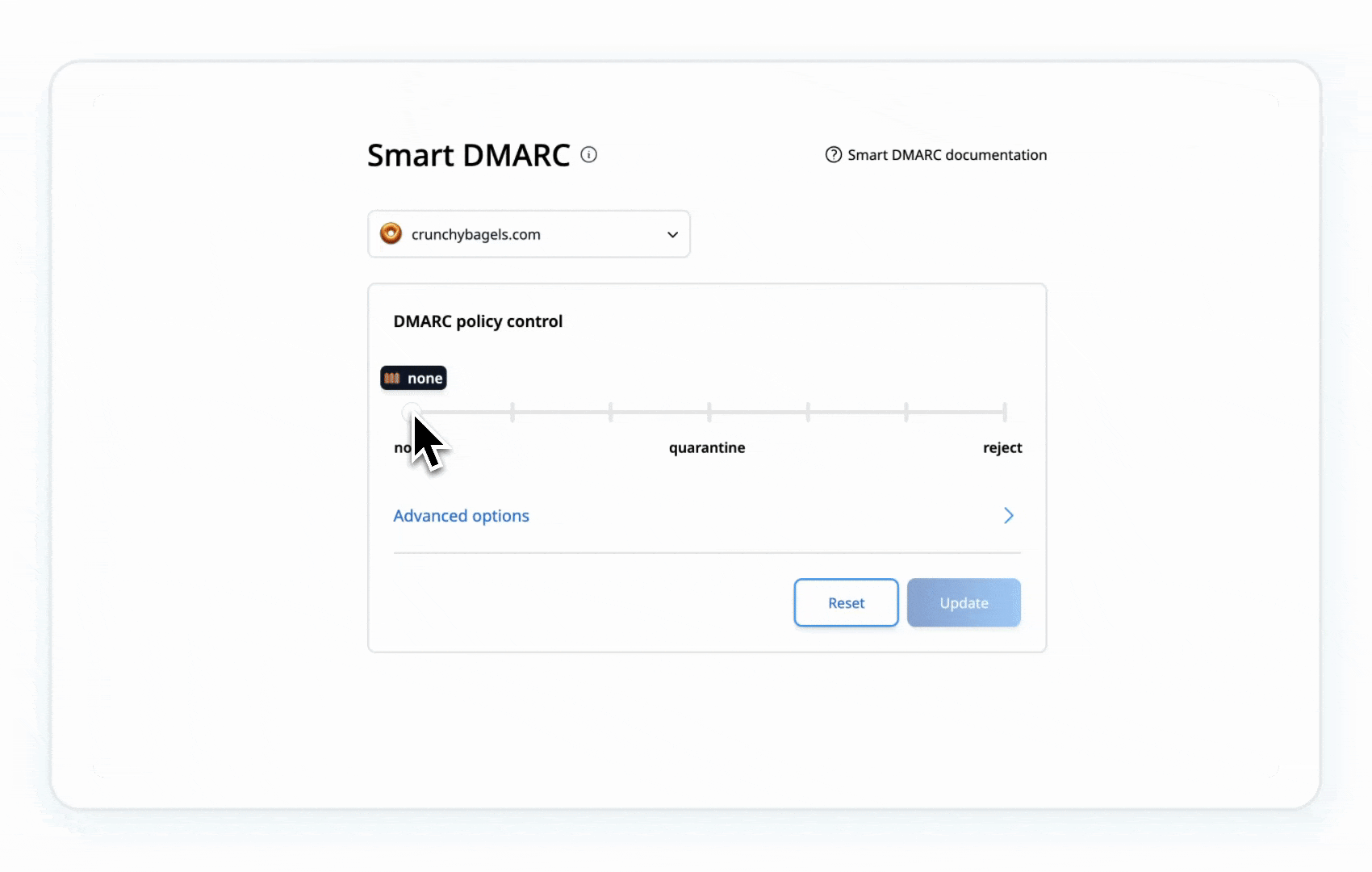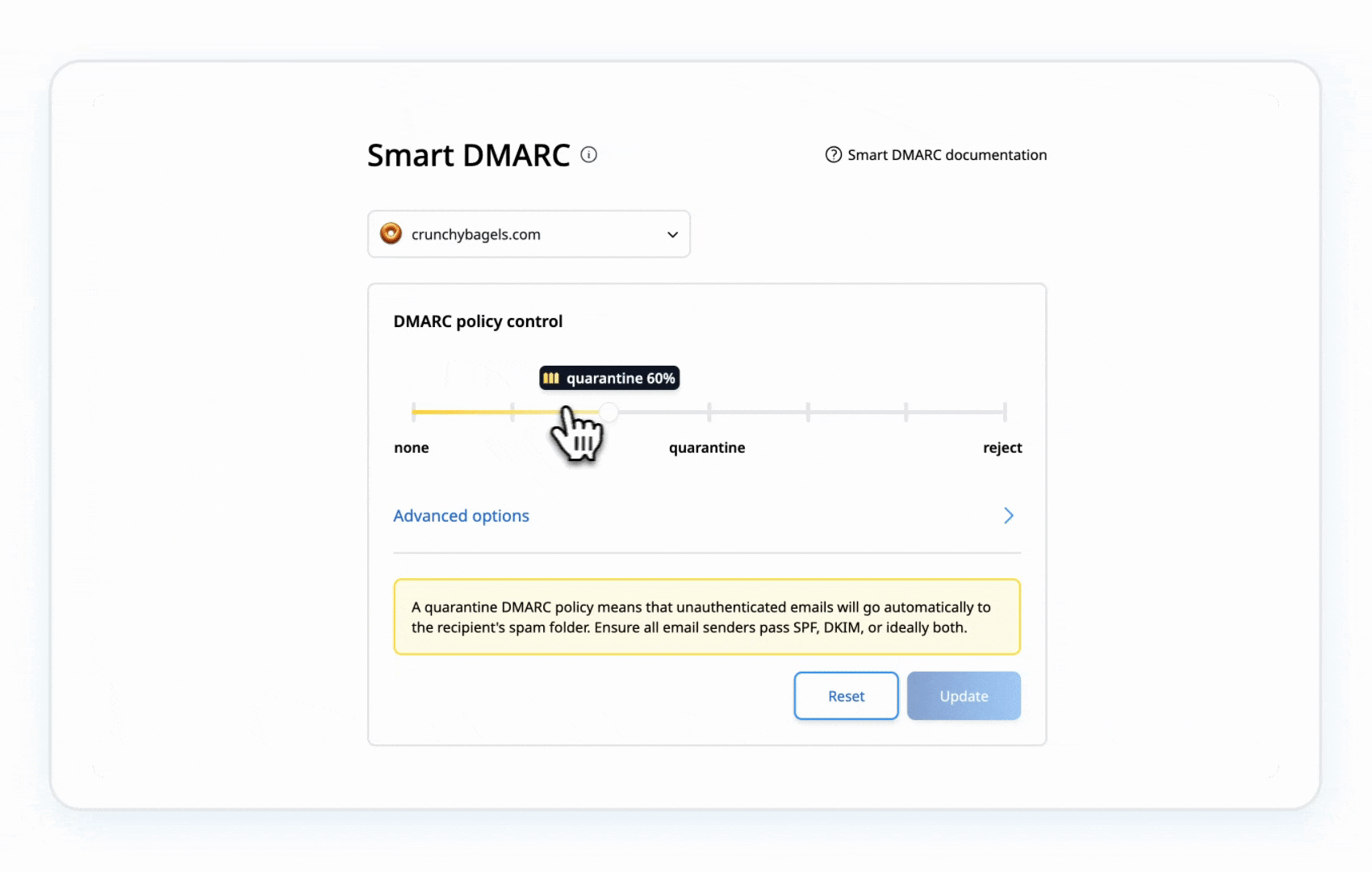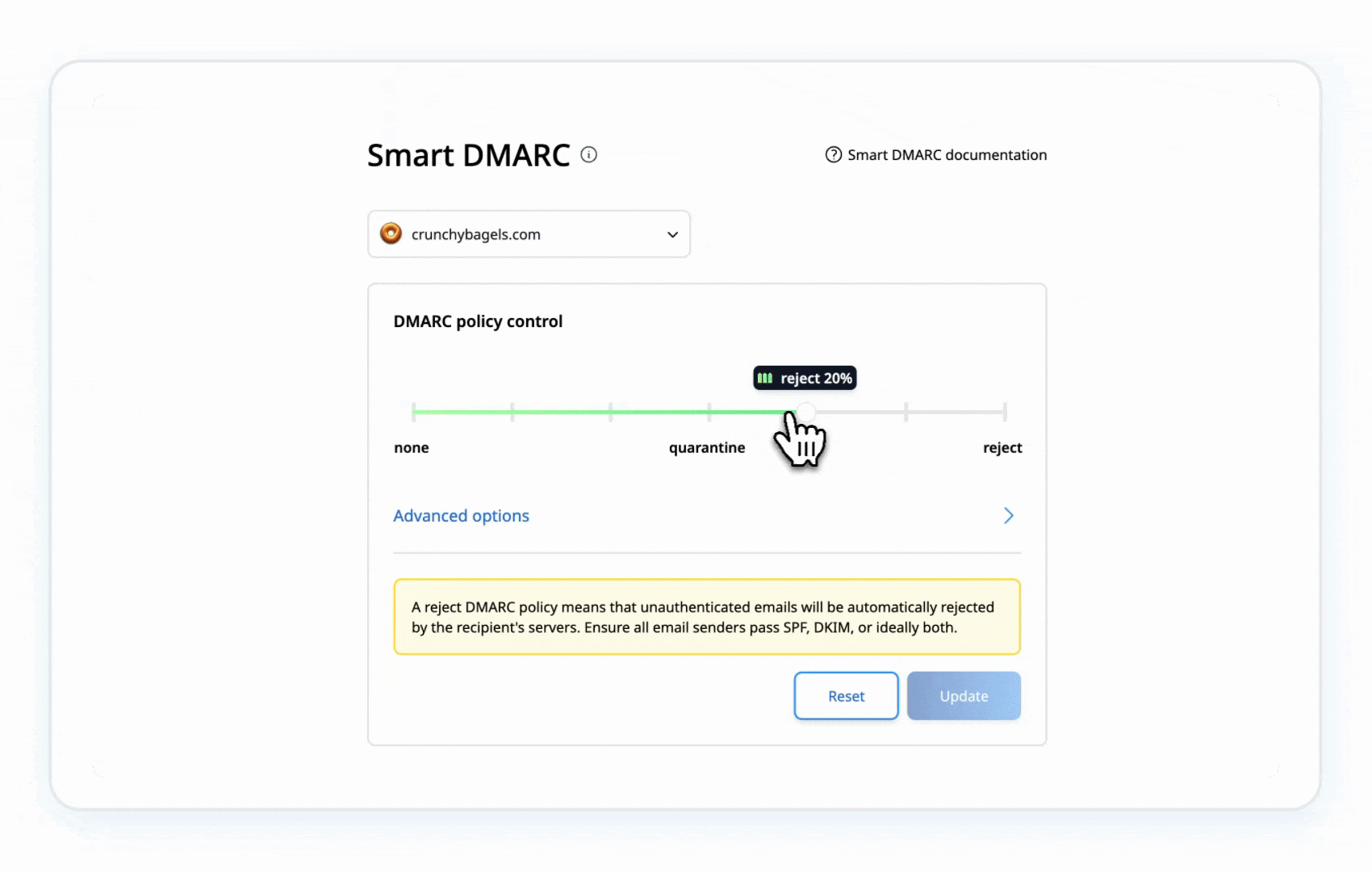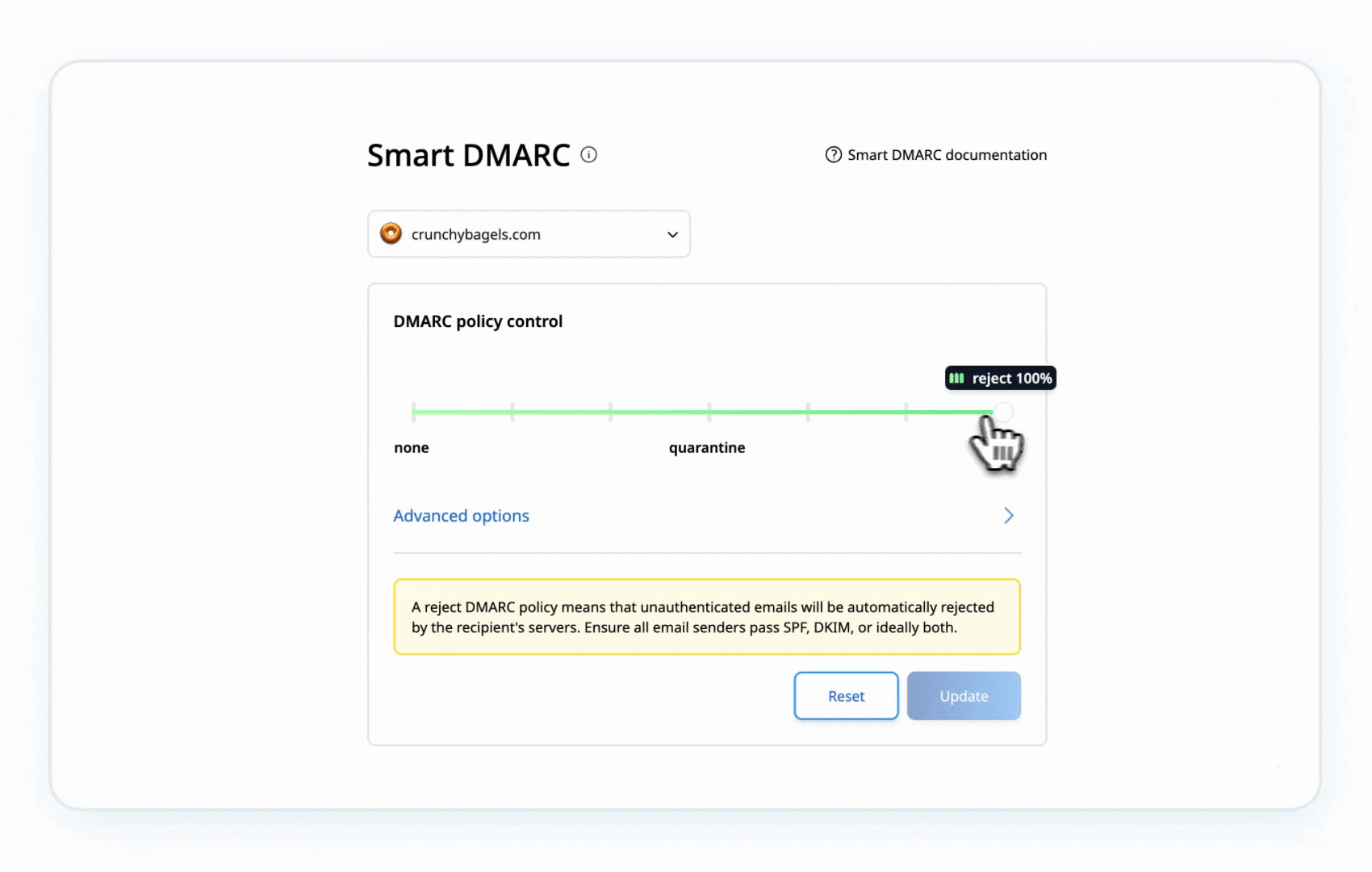
5. Gradually Shift DMARC Policy
Once SPF and DKIM are set up, you can start gradually tighten your DMARC policy step-by-step:
- Move to p=quarantine to send suspicious emails to spam folders.
Example:
- Eventually, shift to p=reject to block unauthorized emails completely.
Example:
This gradual approach lets you monitor the impact and adjust as needed, ensuring legitimate emails keep flowing while locking out impostors.
Even though these steps are straightforward, they can feel technical—especially when juggling DNS records and report analysis. That’s where Palisade’s AI-assisted WorkBench steps in as your compliance partner. With just a few clicks, it simplifies everything:
- Easy Setup: our AI-Assisted Workflow configures SPF, DKIM, and DMARC for you, customized to your domain’s needs.
- Real-Time Monitoring: Get clear, actionable reports to track your email performance.
- Deliverability Boost: Optimize your settings to improve inbox placement and enhance security.
This ensures your business meets standards from providers like Microsoft, Google, and Yahoo without the headaches.
The Big Picture
DMARCbis isn’t a brand-new protocol or a “DMARC2.” It’s a refinement that keeps the core mechanics intact while addressing pain points, and it’s a step forward for email security, making DMARC easier, more flexible, and better suited for today’s complex email landscape. While it doesn’t solve every problem, it lays a stronger foundation for protecting inboxes and it sets the stage for future solutions like ARC or DKIM2..
Get started with Palisade’s AI-Assisted Workflow to ensure DMARC compliance and prepare for DMARCbis.
FAQ
1. What is DMARCbis?
DMARCbis is the updated version of the DMARC (Domain-based Message Authentication, Reporting, and Conformance) protocol, originally introduced in 2015. Developed by the Internet Engineering Task Force (IETF), DMARCbis refines the original protocol with clearer guidelines, new features, and improved flexibility to better protect domains from phishing and spoofing. It’s expected to become a Proposed Standard in 2025.
2. How is DMARCbis different from the original DMARC?
DMARCbis builds on the original DMARC (RFC 7489) with several improvements:
- Clearer Structure: Rewritten for readability with better examples and split into three RFCs (core protocol, aggregate reporting, and failure reporting).
- New Tags: Introduces tags like np (non-existent subdomains), psd (Public Suffix Domains), and t (testing mode), while removing pct, rf, and ri.
- DNS Tree Walk: Replaces the Public Suffix List with a more flexible algorithm for identifying Organizational Domains.
- Stricter Reporting: Updates the XML format for aggregate reports to reflect new tags and real-world practices.
- Guidance on Forwarding: Offers advice on handling email forwarding and mailing list issues, though these remain unresolved.
Despite these changes, DMARCbis remains compatible with existing DMARC records (still using v=DMARC1).
3. Why is DMARCbis important?
DMARCbis makes email security more effective and accessible by:
- Protecting your brand from phishing and spoofing attacks.
- Simplifying DMARC setup for complex domains, like Public Suffix Domains (e.g., gov.uk).
- Providing clearer data to troubleshoot deliverability issues. It also helps ensure compliance with strict DMARC requirements from major providers like Yahoo, Google, and Microsoft, which are critical for email deliverability.
4. Will DMARCbis replace DMARC completely?
No, DMARCbis is an evolution, not a replacement. It refines the original protocol while maintaining compatibility. Existing DMARC records (starting with v=DMARC1) will still work, but you’ll need to update your setup to leverage new features like the np or psd tags once DMARCbis is finalized.
5. What are the challenges of transitioning to DMARCbis?
The transition may involve:
- Learning Curve: New tags (t, np, psd) and the DNS Tree Walk algorithm add complexity.
- Potential Confusion: Replacing the pct tag with t has raised concerns about compatibility with existing setups.
- Mailing List Issues: Email forwarding and mailing lists can still break DMARC alignment, requiring careful policy adjustments.
- Palisade’s AI-Assisted Workflow simplifies this transition by guiding you through new requirements, ensuring compliance, and minimizing disruptions.
6. How does DMARCbis affect compliance with Yahoo, Google, and Microsoft?
Major email providers like Yahoo, Google, and Microsoft have strict DMARC requirements to ensure emails reach inboxes. DMARCbis aligns with these standards by offering clearer guidelines and better reporting, helping you maintain deliverability.
7. When will DMARCbis be finalized?
DMARCbis is in the IETF Last Call phase and is expected to be published as a Proposed Standard in 2025. Until then, avoid making changes based on the draft. When DMARCbis is finalized, Palisade’s AI-Assisted Workflow will guide you through the transition with:
8. Do I need DMARCbis if I already have DMARC set up?
If your DMARC setup is working well, you don’t need DMARCbis immediately. However, adopting DMARCbis will unlock new features like better domain discovery and improved reporting, plus ensure long-term compliance with evolving standards. Palisade can assess your current setup and recommend steps to align with DMARCbis when it’s time.
.png)






.png)

