.png)
Understanding DMARC
DMARC is your domain’s defense against phishing and spoofing, ensuring only legitimate emails reach their destination. However, when DMARC isn’t configured properly, you might encounter delivery failures like the 550 5.7.1 Unauthenticated Email Error.
This issue often arises from incomplete SPF records, misconfigured sender domains, or unauthorized sending servers. In this guide, we’ll explain what the 550 5.7.1 error means, why it occurs, and how to fix it with a clear, actionable approach.
Clarifying the Error Message
When emails bounce, you’ll spot error codes in the non-delivery report (NDR).
Here’s what the 550 5.7.1 error entails:
- 550 5.7.1 Unauthenticated Email Error
- What It Means: This SMTP error indicates that your email failed authentication checks (SPF, DKIM, or DMARC) and was rejected by the recipient’s mail server (MTA).
- Variants: You might see messages like “550 5.7.1 rejected by DMARC policy” or “Unauthenticated mail is prohibited.”
- Why It Happens: The email didn’t pass authentication checks or originated from an unauthorized source, triggering a permanent rejection (the “5.7.1” code).
This error highlights an authentication failure, your email can’t prove its legitimacy. The fix lies in strengthening your domain’s authentication setup.
Diagnosing the Issue
Before applying fixes, identify the root cause:
- Check Email Headers: Examine the headers of a bounced email in your email client (MUA) to review DMARC alignment and authentication results. Look for clues about SPF, DKIM, or server issues.
- Set Up DMARC Monitoring: Add a DMARC record with reporting (e.g., rua=mailto:reports@yourdomain.com) to track failures in real time.
- Review Bounce Messages: These often include details—like specific SPF or DKIM errors—to guide your troubleshooting.
Common Causes and Their Fixes
The 550 5.7.1 error stems from several common issues. Here’s how to address them:
- Unauthorized Sending Server
- Issue: Emails sent from servers not listed in your SPF record fail authentication.
- Fix: Check your SPF record in DNS, add missing servers (e.g., marketing tools), and test with an SPF checker.
- Incomplete SPF/DKIM Configuration
- Issue: Gaps in SPF or a misconfigured DKIM signature disrupt authentication.
- Fix: Ensure SPF includes all senders and DKIM signs emails with a key published in DNS. Validate both with online tools.
- Misconfigured Sender Domain
- Issue: Errors in SPF, DKIM, or DMARC records prevent authentication.
- Fix: Audit your DNS records for typos or mismatches, correct them, and monitor the results.
- Strict Anti-Spam Filters
- Issue: Recipient servers reject emails due to minor DMARC flaws.
- Fix: Start with a lenient DMARC policy (p=none), refine your setup, and adjust content to avoid spam flags.
How to Fix the 550 5.7.1 Error:
Follow this detailed process to resolve the 550 5.7.1 Unauthenticated Email Error and enhance your email authentication. Each step includes instructions, examples, and tips to ensure successful delivery.
Step 1: Audit Your Current Setup
- What to Do: Use tools like Palisade’s Email Score to check your SPF, DKIM, and DMARC records. Enter your domain and review the results.
- What to Look For: Missing records, syntax errors, or incomplete sender lists (e.g., omitting a third-party service like Mailchimp).
- Example: An SPF record like v=spf1 include:_spf.google.com ~all missing your CRM’s server will cause failures.
- Tip: Watch for SPF’s 10-DNS-lookup limit, which can invalidate records.

Step 2: Implement DMARC Monitoring
- What to Do: Add a DMARC record to your DNS with a “none” policy:
- Explanation: p=none monitors without blocking; rua sends reports to the specified email.
- How: Create a TXT record for _dmarc.yourdomain.com via your DNS provider (e.g., Cloudflare).
- Tip: Use a dedicated email for reports to stay organized.
Step 3: Analyze DMARC Reports
- What to Do: Review XML reports sent to your rua address for:
- Failed SPF or DKIM authentications.
- Unauthorized sending servers.
- Domain alignment issues.
- How: Use Palisade Workbench for a simplified view.
Step 4: Correct SPF and DKIM Configurations
- Update your SPF record to include all senders:
- List mail server IPs and include third-party services.
- Flatten records if nearing the 10-DNS-lookup limit.
- Fix DKIM:
- Ensure emails are signed with a valid DKIM key, published in DNS (e.g., selector1._domainkey.yourdomain.com).
- Verify signatures with a DKIM checker.
- Validation: Test both with Palisade SPF Checker and DKIM Checker to confirm accuracy.
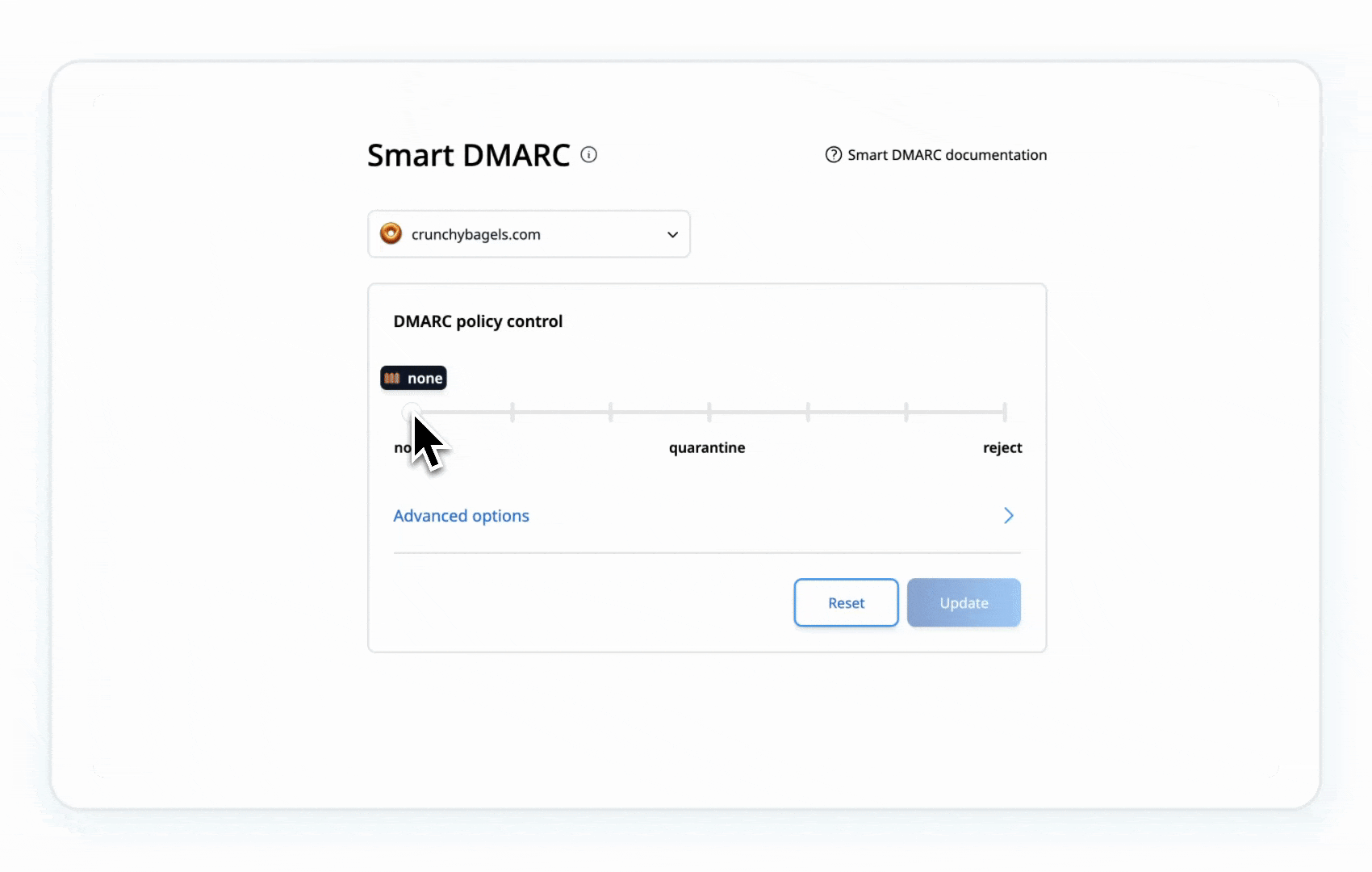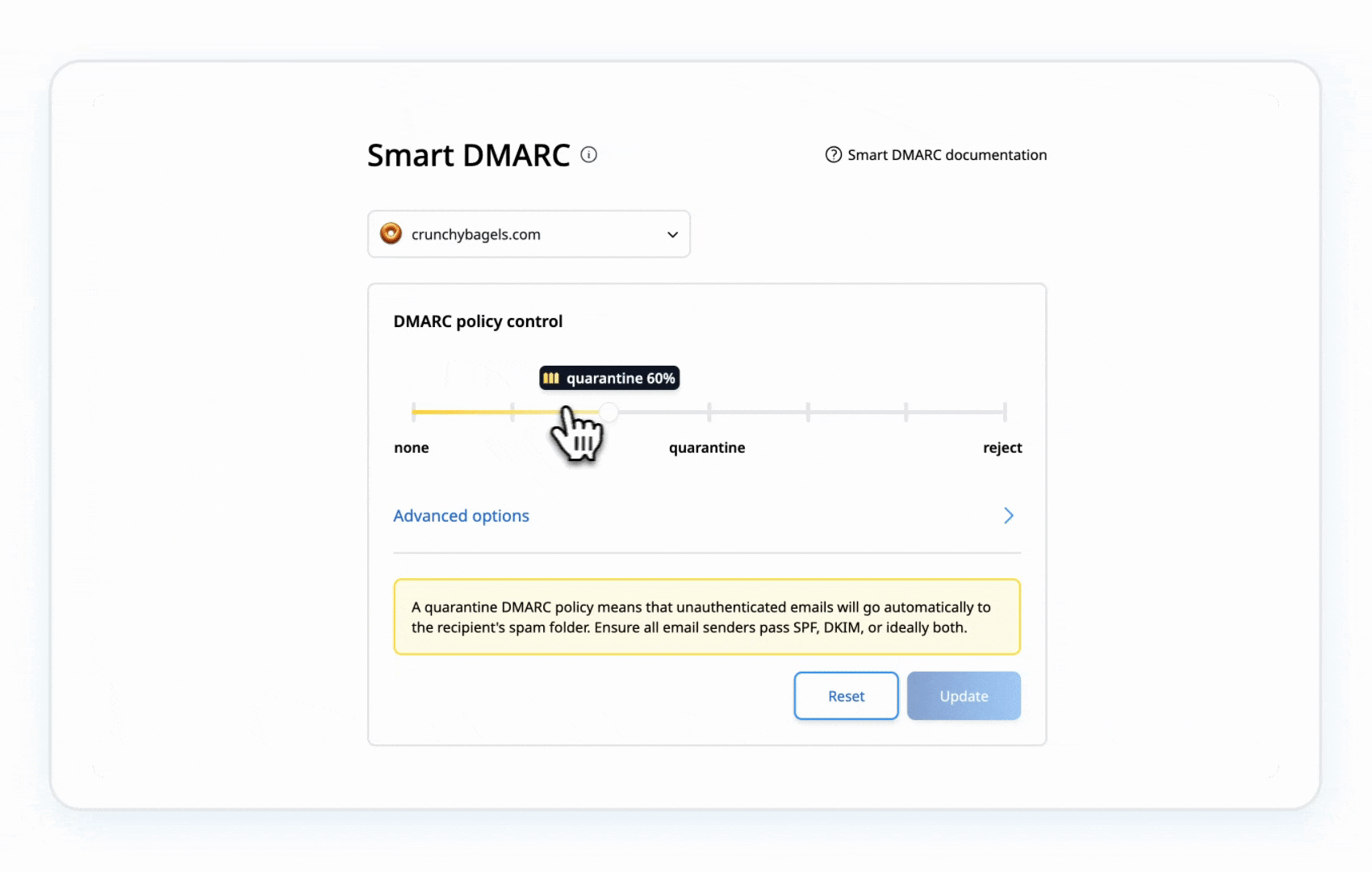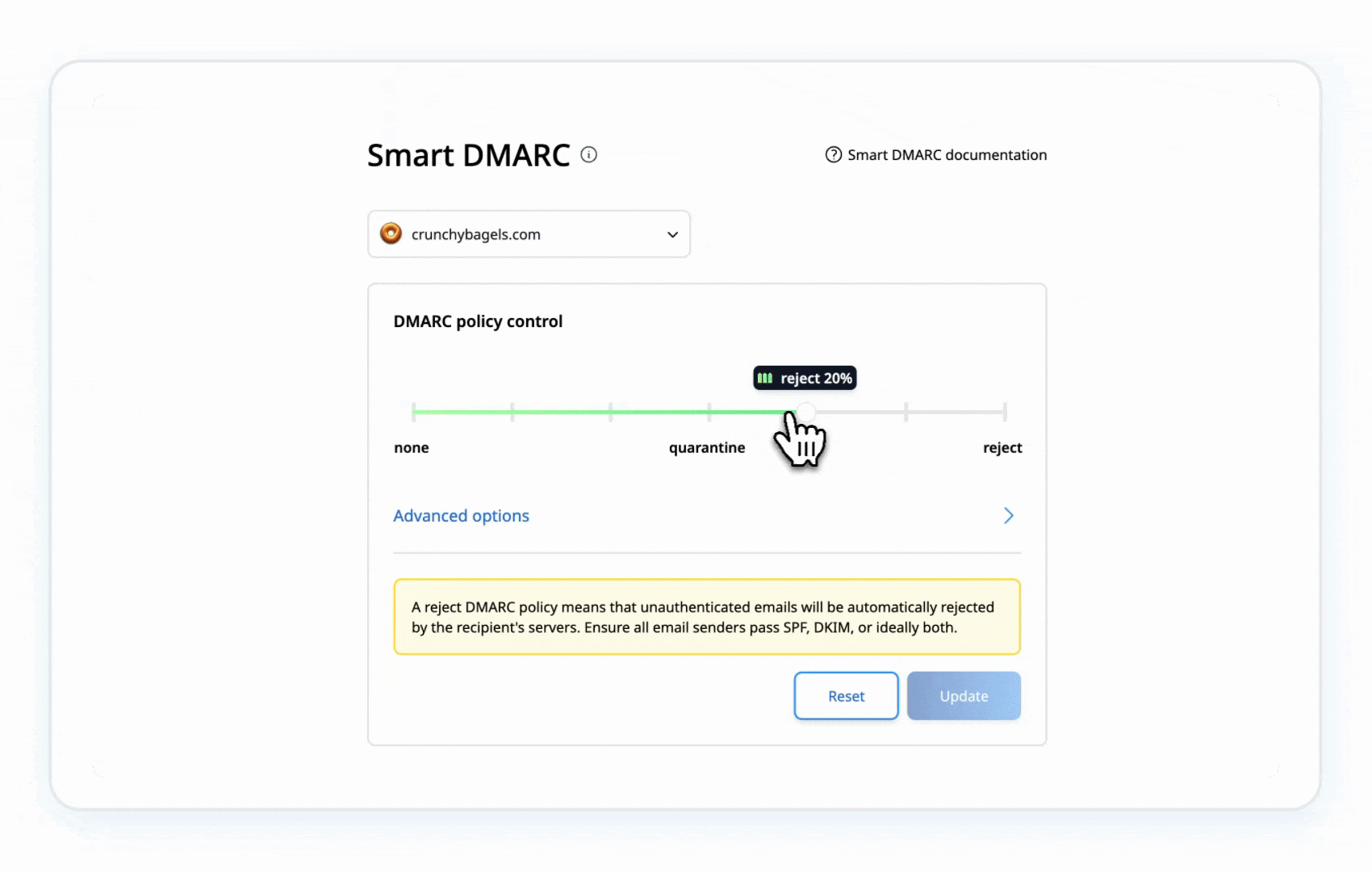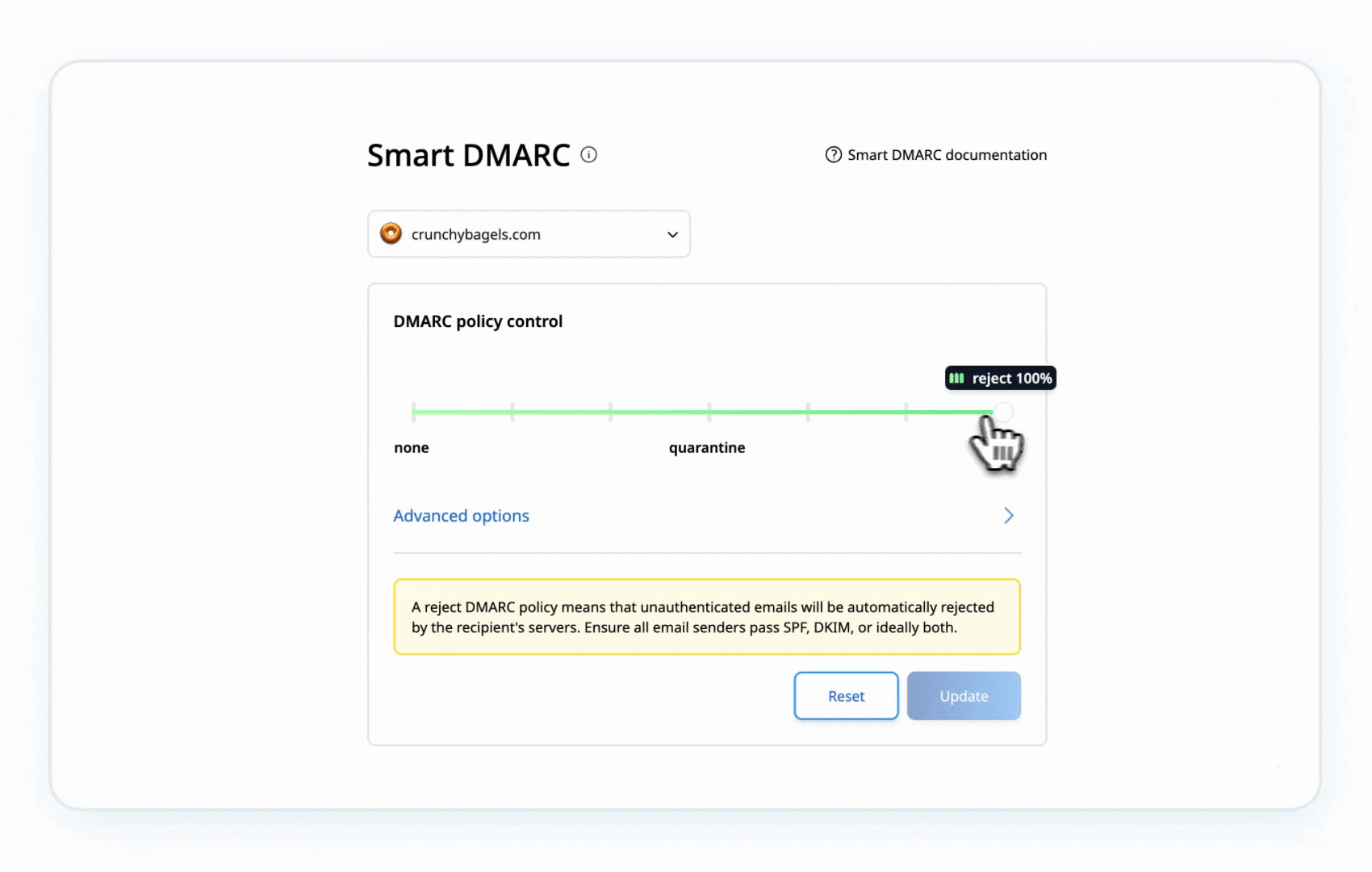
Step 5: Strengthen Your DMARC Policy
- Gradually update your DMARC record to p=quarantine:
- Move to p=reject after confirming no legitimate emails are flagged:
- Blocks unauthenticated emails.
- Moves suspicious emails to spam/junk.
Step 6: Test and Validate
- What to Do:
- Send test emails to a personal account.
- Check headers in your email client (MUA) for:
Authentication-Results: spf=pass; dkim=pass; dmarc=pass
Step 7: Maintain Ongoing Security
- What to Do:
- Review DMARC reports weekly.
- Update SPF for new senders.
- Rotate DKIM keys every 6-12 months.
- Clean email lists to remove inactive addresses.
While the steps above might seem straightforward, DMARC setup can sometimes be tricky. That’s where Palisade comes in to save the day. Our AI-Assisted Workflow takes the complexity out of the equation by automating the entire process, from setup to ongoing monitoring, ensuring your emails comply with DMARC standards and land safely in their intended inboxes.
Other Best Practices for Ongoing Email Security
Keep errors at bay with these practices:
- Monitor Regularly: Check DMARC reports weekly for new issues.
- Update SPF: Adjust for new senders as your setup evolves.
- Refresh DKIM: Rotate keys every 6-12 months.
- Clean Your List: Remove inactive addresses to boost reputation.
- Mind Your Content: Avoid spammy phrasing or excessive links.
Conclusion
The 550 5.7.1 Unauthenticated Email Error can disrupt your communication, but it’s fixable. By understanding the error, diagnosing the problem, and applying targeted fixes, you can protect your brand and ensure delivery. Palisade removes the guesswork, quickly fixing your setup and keeping your emails inbox-bound.
Ready to stop the bounces? Try the Palisade’s AI-Assisted Workflow and secure your email today.
Frequently Asked Questions (FAQ)
1. What is the 550 5.7.1 Unauthenticated Email Error?
The 550 5.7.1 error is an SMTP code indicating that your email was rejected by the recipient’s mail server due to failing DMARC authentication. It often comes with messages like “Unauthenticated mail is prohibited” or “Rejected by DMARC policy.”
2. Why does the 550 5.7.1 error occur?
This error occurs when your email fails SPF, DKIM, or DMARC authentication checks. Common causes include misconfigured DNS records, unauthorized sending servers, or incomplete email authentication setups.
3. How can I fix the 550 5.7.1 error?
To resolve this error:
- Ensure your SPF record includes all authorized sending servers.
- Verify your DKIM signature and publish the correct public key in DNS.
- Set up a DMARC policy and monitor reports to identify and fix issues.
4. What is DMARC and why is it important?
DMARC is an email authentication protocol that protects your domain from phishing and spoofing. It ensures only legitimate emails are delivered, helping maintain your brand’s reputation and email deliverability.
5. How do I check my SPF, DKIM, and DMARC records?
Use Palisade’s Email Score to audit your DNS records. These tools will show you any missing or incorrect entries causing authentication failures.
6. What is an SPF record and why is it important?
An SPF record lists the servers authorized to send emails for your domain. It’s essential for passing authentication checks and preventing your emails from being rejected or marked as spam.
7. What should I do if my emails still fail after fixing SPF and DKIM?
Check for domain alignment (e.g., matching “From” domains), review your DMARC policy, and analyze DMARC reports to identify any remaining issues, such as unauthorized senders.
8. How long does it take for DMARC changes to take effect?
DNS changes, including DMARC updates, can take up to 48 hours to propagate globally. Test your emails and monitor reports to confirm when the changes are active.
9. Can tools help with fixing DMARC errors?
Yes! Tools like Palisade’s AI-Assisted Workflow can automate DMARC setup, monitoring, and maintenance, ensuring your emails pass authentication and reach inboxes reliably.
.png)






.png)


